wireless sensor network
Overview
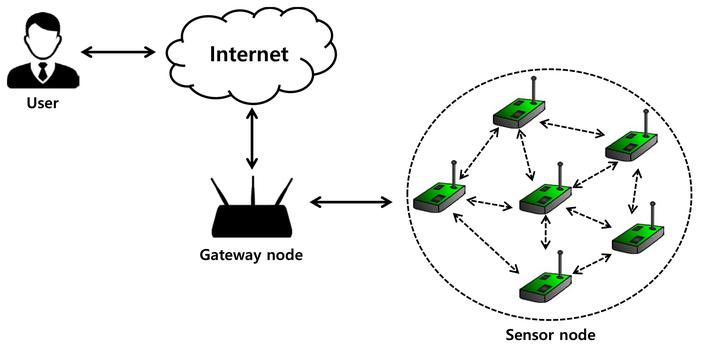
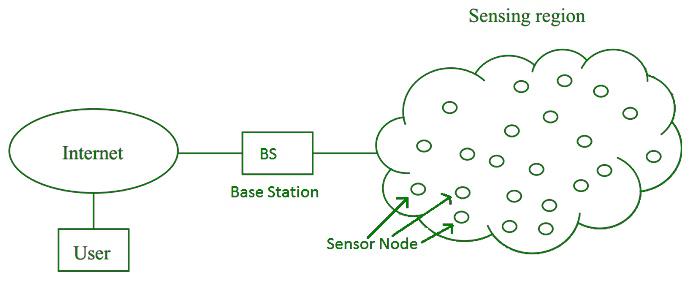
Wirelesssensornetworkisaformofnetworkformedbyfreelyorganizingandcombiningtensofthousandsofsensornodesthroughwirelesscommunicationtechnology.Theunitsconstitutingthesensornodeare:adataacquisitionunit,adatatransmissionunit,adataprocessingunit,andanenergysupplyunit.Amongthem,thedataacquisitionunitusuallycollectsandconvertstheinformationinthemonitoringarea,suchaslightintensity,atmosphericpressureandhumidity,etc.;thedatatransmissionunitmainlyuseswirelesscommunicationandexchangeofinformation,aswellassendingandreceivingthecollecteddatainformation;Thedataprocessingunitusuallyhandlesroutingprotocolsandmanagementtasksandpositioningdevicesforallnodes;theenergysupplyunitselectstheformofmicro-batteryinordertoreducetheareaoccupiedbythesensornodes.Therearetwotypesofnodesinthewirelesssensornetwork,oneisthesinknodeandtheotheristhesensornode.Thesinknodemainlyreferstothatthegatewaycaneliminatethewrongreportdataamongthesensornodes,andcombinethedatawithrelatedreportstomakejudgmentsontheoccurrenceofevents.Thesinknodeandtheusernodecancommunicatedirectlywiththehelpofawideareanetworkorsatellite,andprocessthecollecteddata.
Thesensornetworkrealizesthethreefunctionsofdatacollection,processingandtransmission.It,togetherwithcommunicationtechnologyandcomputertechnology,constitutesthethreepillarsofinformationtechnology.WirelessSensorNetwork(WirelessSensorNetwork,WSN)isawirelessnetworkcomposedofalargenumberofstationaryormovingsensorsinaself-organizingandmulti-hopmannertocooperativelysense,collect,processandtransmitthenetworktocoverthesensedobjectsinthegeographicalarea.Information,andultimatelysendthisinformationtotheownerofthenetwork.
Thewirelesssensornetworkhasmanytypesofsensorsthatcandetectthesurroundingenvironmentincludingearthquake,electromagnetic,temperature,humidity,noise,lightintensity,pressure,soilcomposition,size,speedanddirectionofmovingobjectsAvarietyofphenomenainthe.Potentialapplicationareascanbesummarizedas:military,aviation,explosion-proof,disasterrelief,environment,medical,health,household,industrial,commercialandotherfields.
Features
Comparedwithtraditionalnetworksandothersensors,wirelesssensornetworkshavethefollowingfeatures:
(1)Freedomofformation.Theformationofwirelessnetworksensorsisnotrestrictedbyanyexternalconditions.Theorganizercanquicklysetupafullyfunctionalwirelessnetworksensornetworknomatterwhenandwhere,andthemaintenanceandmanagementworkafterthesuccessfulformationiscompletelycarriedoutwithinthenetwork..
(2)Theuncertaintyofthenetworktopology.Fromtheperspectiveofthenetworklevel,thenetworktopologyofwirelesssensorsischangeable.Forexample,thesensornodesthatmakeupthenetworktopologycanbeincreasedordecreasedatanytime,andthenetworktopologycanbeseparatedormergedatanytime.
(3)Thecontrolmethodisnotcentralized.Althoughthewirelesssensornetworkcentrallycontrolsthebasestationandsensornodes,thecontrolmethodbetweeneachsensornodeisstilldecentralized.Thefunctionsofroutingandhostarerealizedbytheterminalofthenetwork.Eachhostrunsindependentlywithoutinterference.Therefore,wirelessThestrengthofthesensornetworkisveryhighanditisdifficulttobedestroyed.
(4)Thesecurityisnothigh.Thewirelesssensornetworktransmitsinformationwirelessly,sothesensornodesareeasilyinvadedbytheoutsideworldintheprocessoftransmittinginformation,whichleadstoinformationleakageanddamagetothewirelesssensornetwork.Mostofthenodesofthewirelesssensornetworkareexposed.Itgreatlyreducesthesecurityofthewirelesssensornetwork.
Compositionstructure
Wirelesssensornetworkismainlycomposedofthreeparts,includingnodes,sensornetworksandusers.Amongthem,nodesgenerallycoveracertainrangeofnodesinacertainway,andtheentirerangecanmeetthemonitoringrangeaccordingtocertainrequirements;thesensornetworkisthemostimportantpart,whichcollectsallnodeinformationthroughfixedchannels.Thenperformcertainanalysisandcalculationonthesenodeinformation,summarizetheanalyzedresultstoabasestation,andfinallytransmittothedesignateduserterminalthroughsatellitecommunication,soastoachievetherequirementsofwirelesssensing.
InformationSecurity
SecurityRequirements
BecauseWSNuseswirelesscommunication,itscommunicationlinkisnotasprivateandcontrollableaswirednetworks.Therefore,whendesigningasensornetwork,itisnecessarytofullyconsidertheissueofinformationsecurity.SmartcardssuchasmobilephoneSIMcardsusethePublicKeyInfrastructure(PKI)mechanismtobasicallymeettheinformationsecurityneedsofindustriessuchastelecommunications.Similarly,PKIcanalsobeusedtomeettherequirementsofWSNintermsofinformationsecurity.
(1)Dataconfidentiality
Dataconfidentialityisanimportantnetworksecurityrequirement.Allsensitiveinformationmustbekeptconfidentialduringstorageandtransmission.Thecontentofinformationdisclosedbyunauthorizedusers.
(2)Dataintegrity
Withtheguaranteeofconfidentiality,theattackermaynotbeabletoobtainthetruecontentoftheinformation,butthereceivercannotguaranteethatthedataitreceivesiscorrect,Becausemaliciousintermediatenodescanintercept,tamper,andinterferewiththeinformationtransmissionprocess.Throughdataintegrityauthentication,youcanensurethatthereisnochangeinthedatatransmissionprocess.
(3)Datafreshness
Theproblemofdatafreshnessistoemphasizethatthedatareceivedeachtimeisthelatestdatasentbythesender,soastopreventreceivingduplicateinformation.Themainpurposeofensuringdatafreshnessistopreventreplayattacks.
(4)Availability
Availabilityrequiresthatthesensornetworkcanprovideinformationaccessservicestolegitimateusersofthesystematanytimeinapre-setworkingmode,butattackerscanuseforgeryandsignalinterferenceInotherways,thesensornetworkispartiallyorcompletelyparalyzed,destroyingtheavailabilityofthesystem,suchasDenialofService(DoS)attacks.
(5)Robustness
Wirelesssensornetworkshavestrongdynamicsanduncertainties,includingchangesinnetworktopology,disappearanceorjoiningofnodes,andvariousthreats.Therefore,thewirelesssensornetworkshouldhavestrongadaptabilitytovarioussecurityattacks.Evenifacertainattackissuccessful,theperformancecanensurethatitsimpactisminimized.
(6)Accesscontrol
Accesscontrolrequirestheidentificationofuserswhoaccessthewirelesssensornetworktoensureitslegitimacy.
Threats
Accordingtothedifferentnetworklevels,thethreatsthatwirelesssensornetworksarevulnerabletocanbedividedintofourcategories:
(1)Physicallayer:mainTheattackmethodiscongestionattackandphysicaldestruction.
(2)Linklayer:Themainattackmethodsarecollisionattack,exhaustionattackandunfaircompetition.
(3)Networklayer:Themainattackmethodsaredropandgreedydestruction,directionmisdirectionattacks,blackholeattacksandaggregationnodeattacks.
(4)Transportlayer:Themainattackmethodsarefloodingattacksandsimultaneousdestructionattacks.
Keytechnology
1.Chaoticencryptiontechnology
Cryptographyisaninterdisciplinarysubject,anditsexplorationismainlythroughsomemeansandmethodsUsefulinformationishidden,andonlythroughtheauthorizationofthelicensorcanthecontentintheinformationbecorrectlyinterpreted,andthetechnologythattransformstheinformationintoanunreadableformiscalledencryptiontechnology.Amongthemanychaoticencryptiontechnologiesinwirelesssensors,themostrepresentativeoneisthesymmetrickeysystemtechnology,whichisalsoacryptographicalgorithm,whichconsumeslowenergyandisrelativelynotverycumbersometocalculate.Thecriteriaforjudgingwhetherthecryptographictechnologyusedbythewirelesssensornetworkisthemostappropriateusuallyhavethefollowingaspects:thelengthofthedataoccupationandtheprocessingtime,theamountofenergyconsumed,andthelengthofthecryptographicalgorithmcode.Thecryptographicalgorithmsincludeadvancedencryptionalgorithms,symmetricencryptionalgorithms,andsoon.Chaoscryptographyisarelativelycomplextechnologyasawhole,itabidesbythedynamicmechanismandthebasicprinciplesofchaosanddiffusion.
2.Keymanagementprotocol
Keymanagementprotocolistoperformhierarchicalauthorizationprotectionforallstepsfromwhenthekeyisgeneratedtouse,toensuretheclosednessofthekeyandalsotodoToflexibleuse.Forexample,thegenerationanddistributionofkeysareauthorizedbyfinancialinstitutionstoenablethemtogeneratekeysanddistributethemtothepayingpartyintransit,sothattheycangeneratedigitalsignaturestoensurethenon-repudiationoftheinformation,andthefinalkeynotarizationisauthorizedwithspecificinstitutionstoverifyTheauthenticityoftheinformation.Thedataverificationprotocolisaprotocolforthesecurityverificationofthedatauserswilluse,verifyingwhetherthedataexchangedinthebigdataerahasend-levelsignaturesandpersonalsignatures.Securityauditprotocol,thecontentoftheprotocolistocollect,detectandcontrolallsecurity-relatedeventsinthebigdataera,playaroleintheprotectionofdangersandholdaccountabilityforeventsthatendangersecurity.
3.Digitalwatermarkauthenticationtechnology
Digitalwatermarkauthenticationtechnologyembedsidentificationinformationintotheoriginalcarrierthroughalgorithms,whichisconvenientforlegaluserstoextractandidentify.Theuseofdigitalwatermarkingtechnologycanensurewhethertheauthenticationinformationhasbeentamperedwith,therebyimprovingthetransmissionreliabilityofthewirelesssensornetwork.Thedigitalwatermarkingtechnologyismainlycomposedoftwoparts:anembedderandadetector.Combinedwithcryptography,multiplesecurityprotectionsforinformationcanberealized.Generally,forthetransmissionofinformation,awatermarkembedderisusedtoformacombinationofthewatermarkkeyandtheoriginalcarrierdata,andthewatermarkisdecryptedaccordingtothewatermarkdetectortooutputtheinformationwheninuse.
4.Firewalltechnology
Inspecificapplications,thistechnologyhasastrongAAAmanagementfunction,whichtranslatestheIPaddressoftheinternalhosttotheexternalnetwork,makingthewirelesssensornetworkSharingtheInternetcanalsocausetheexternalnetworktobehiddenintheinternalnetworkstructure:itcansupportavarietyofAAAprotocolstodialintotheASAforvariousremoteaccessVPNs,logintotheASAmanagementsessiontoauthenticateandauthorizeAAA.Inthewirelesssensornetwork,thefirewalltechnologycanensurethatthenetworkwillnotbeattackedbyworms,hackers,virusesandbadparts,anditalsocontainsaclientlessmodeVPNtoensurethatwirelesssensornetworkcustomersdonotneedtoinstallaVPNclient.Providethemwithnetworkservices.Inthecompositionofthewirelesssensornetwork,thewirelessnetworkcanbeeffectivelyseparatedfromthecorenetwork,andoneorseveralwirelessnetworkscanbemanagedseparatelythroughthefirewall,sothatevenifthewirelessclientissuccessfullycracked,itcannotbeattacked.Wirednetwork.
Applicationrange
1.Theapplicationofwirelesssensorsinelectricalautomation
Intheprocessofcontinuousdevelopmentofautomationtechnologyinmycountry,mycountry’spowersystemisdevelopingrapidlyInonearea,theautomationofthepowersystemhelpstoreduceunnecessaryenergywaste,reducetheincidenceofaccidents,andimprovetheefficiencyofrepairsandmaintenanceintheeventofanaccident.Thefaulttolerancerateofmanualpowersystemmanagementislow.Peoplemustmaketimelyadjustmentsaccordingtotheoperatingconditionsofthepowersystemequipmentintheprocessofwork.Similarly,intheprocessofelectricalautomation,thepowersystemneedstobemonitoredinrealtime,andthepowersystemneedstobemonitoredinrealtime.Thevoltageisadjusted.Duringtheoperationofthepowersystem,duetotheexternalenvironmentsuchasweathertemperature,etc.,itwillchangefromtimetotime.Iftheexternalconditionschangedrastically,thevariouspowerattributesinthepowersystemwillalsoundergomajorchanges.Inordertocompensateforthispartofthechange,itneedstobeadjusted.Thecollectionofdataisfirstofallanimportantcontent.Thereneedstobesomedevicesthatcancountthevaluesofvariouselectricalpropertiesintheelectricalsystem,andthenprocessthemtoprocessthedata.Recordthetransmission,controlitaccordingtothecontentofthetransmission,andimproveitslevelofautomation.Inaddition,itisalsonecessarytosetupsomeenvironmentalsensingdevicessuchastemperatureandhumidityintheunitdistancetomonitortheenvironmentofthepowersysteminordertopredictchangesinthepowersystem.Inelectricalautomation,wirelesssensingdevicesaremostlyused,whichcanavoidsomewiringproblemsandimprovetheefficiencyofthesensingdevices.Comparedwiththepastmonitoringandmanagementdevices,theuseofwirelesssensingdeviceshasmoreadvantages.Oneofthemoreobviousadvantagesistoreducethecomplexityoftheline.Inthepowersystem,especiallythehigh-voltagetransmissionline,ifthelineismoreComplicated,intheprocessofmanagementandmaintenance,itwillincreasethedifficultyofthework,andithasahigherrisk.Comparedwiththetraditionalsensingdevice,thewirelesssensingdeviceislesslikelytobedamaged,andthetransmitteddataismoreaccurate,whichmakesitmorevaluable.
2.Applicationofwirelesssensingtechnologyinmonitoringwork
Intheprocessofmonitoringusingwirelesssensingtechnology,themonitoringequipmentusedindifferenttypesofmonitoringworkisnotonlysame.Amongthem,intheprocessofindustrialproduction,themorecommonlyusedsensingtechnologyistemperaturesensingtechnology.Intheprocessofusingsensingtechnologytomonitorindustrialproduction,themonitoringismainlyfortheboilertoensurethesafetyoftheboiler.Intheboiler,theboiler'swater-cooledpipeiscloselyrelatedtotheboilertemperature.Mostofthecommonwater-cooledpipestodayarecomposedofsteelpipes.Duringtheprocessofdischargingheat,itneedstobedischargedthroughthesteelpipe.However,asalargeamountofheatisdischargedduringthecoolingprocess,somesundries,suchassomefinesootparticles,etc.,maybedischargedatthesametime.Overtime,somedirtmayappearinsidethewaterwalltoadheretothesteelpipe.Ifthedirtaccumulatestoothick,Itwillaffecttheheatdissipationofthesteelpipe,andtheheatthatthewaterwallcanwithstandoftenhasacertainupperlimit.Theheatonthewaterwallisdifficulttoloseintime,anditwillworkunderexcessivepressureandoverloadforalongtime.Thestatuswillhaveamoreseriousimpactonthestructureofthewaterwall.Afteraperiodofuse,moreseriousaccidentsmayoccur.Nowadays,themanagementofboilerworkmostlyusescomputersforremotecontrol,whichcanpreventthehightemperatureenvironmentfromcausingharmtothestaff.However,theuseofremotecontroltechnologyrequiresmonitoringoftheboiler.Inahigh-temperatureenvironment,theuseofwiredmonitoringdeviceswillcausethelinetobeaffectedbythehigh-temperatureenvironment,causingadditionallossesandrequiringmoreinvestment.Theuseofwirelesssensortechnologyformonitoring,intheprocessofdatatransmission,withoutotheritemsasamedium,candirectlytransmitmeasurementdata,sothatintheprocessofmonitoringandmanagement,thenumberofdamagedpartswillbereduced,whichcaneffectivelyreduceproductioncost.Moreover,thewirelesssensornetworkcanbeusedtomonitordifferentpartsmorecomprehensively,makingtheworkmorecomprehensive.
3.Theapplicationofwirelesssensingtechnologyinpositioning
Theapplicationofwirelesssensingtechnologyintoday'sapplicationcannotonlybeusedbylargeorganizationsforworkandscientificresearch.Forindividuals,duetothecontinuousdevelopmentoftechnology,thecostofwirelesssensingtechnologyisgettinglowerandlower,andmoreandmorepeoplecanusewirelesssensingtechnologyonindividuals.Forindividuals,themainpurposeofwirelesssensingtechnologyisforpositioning.Positioningtechnologyisamorewidelyusedaspectofsensingtechnology.Theinstallationofwirelesssensingdevicesonvehiclescanbeachievedthroughwirelesssensingtechnology.Thelocationinformationofthevehicleistransmitted,andthentheinformationisprocessedandsentbythetransferstation,sothatthelocationinformationofthevehiclecanbeclearlyunderstoodatthereceivingstation.Itisofgreatsignificanceforcarnavigation.Inaddition,wirelesssensingtechnologycanbeusedforsomecarry-onitemstolocatesomeelderlyorchildreninrealtime,soastoavoidaccidentsforsomevulnerablepeople.
Latest: routing
Next: Priori probability








