Password protocol
two or more participants set a series of steps convention to complete a particular task in password communication.
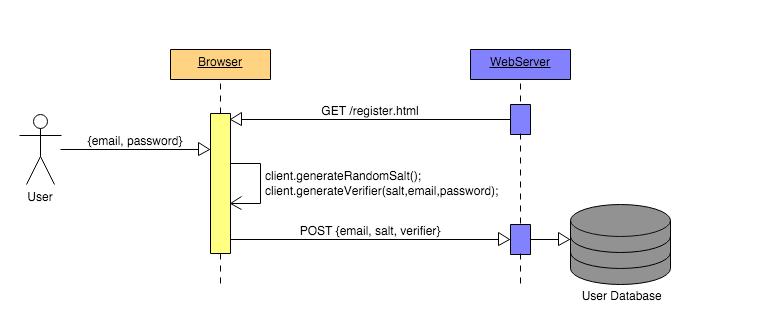
Password protocol typically refers to between password devices, between password managers, password managers and managers, and password systems and users, to complete key delivery, data Transmission, or status information, control information exchange, etc. related to password communication, the agreed communication format, step, and the predetermined password operation method, the key data used. The characteristics of the password protocol are: 1 confidential. Both of the agreement use key implementation password operation, only the information exchanged information is known. 2 trusted. The agreement must ensure that the communication between communication is credible, and the content of communication is credible. 3 Order. The implementation steps of the agreement should be rigorous, complete, and in an orderly manner. 4 Efficient. The implementation agreement takes a minimum time, and cannot affect the total time overhead of the system due to the execution of the branch protocol. The design of the password protocol is an important part of the cryptographic system design. It is generally necessary to implement formal analysis and verification of the password protocol to ensure the security of the password protocol. The execution of the password protocol is also the subject activity of the cryptographic system, which is generally implemented by the computer program.
Publisher: China Military Encyclopedia Book Review Room
Latest: Back to Bedlam
Next: Multi-characteristic







