Anonymous P2P
Category
The central degree
-
-
pure P2P
-
node as both client and server side.
-
is no central server.
-
no central router.
-
as Gnutella.
-
-
-
heteroaryl P2P
-
a central information server node and saved request information required to respond.
-
node responsible for publishing this information (because the central server does not save the file), so that the central server know what they want to share files, so it needs to download the nodes can share resources .
-
terminal uses the routing address, to obtain the absolute address is referenced by a set index.
-
The most primitive Napster.
-
-
-
Hybrid P2P
-
also contains the characteristics of pure P2P and heteroaryl of P2P.
-
as Skype.
-
The Network Topology
-
-
structure P2P
< / li> -
mutual coupling between the point information, specific rules are formed with each other topologies. When
-
needs to request a resource, according to the topology rules to find, if present, is able to find.
-
as Chord, YaCy, Kademlia.
-
-
-
unstructured P2P
-
mutual information between the coupling point, another forming irregular mesh topology. When
-
node needs to request a resource, in a broadcast manner to find usually set TTL, even if there is not able to find.
-
as Gnutella.
-
-
-
loosely structured P2P
-
mutual information between the coupling point, another forming irregular mesh topology. When
-
needs to request a resource, according to the conventional estimation of the information seeking, between the structural and non-structural P2P P2P interposed.
-
as Freenet.
-
advantage
-
have the preferred parallel processing capabilities.
-
use memory to manage the exchange of information, greatly improving performance.
-
do not have to invest a lot of money in software and hardware device server.
-
suitable for small-scale network, easy to maintain.
disadvantages
-
architecture is more complex, we must have a server-side development, but also a special client.
-
is used in large-scale network, share resources disorders, difficult to manage, less secure.
Application
Point technology has many applications. Share contain various formats of audio, video and data files are very common, real-time data (such as IP telephony, Anychat audio and video software developers) can use P2P technology to transfer.
Some networks and channels of communication, such as Napster, OpenNAP, and IRC @ find, on the one hand using a master-slave architecture structure to handle some tasks (such as search), on the other hand while using P2P structure to handle other tasks. And some networks such as Gnutella and Freenet, using P2P structure to handle all the tasks, sometimes considered a true P2P network. Although Gnutella also use the directory server to obtain convenient node network addresses of other nodes.
2015 Nian 1 28, of Pennsylvania State University developers, a joint MIT Open Knowledge action, researchers at Simon Fraser University, as well as second-generation Internet P2P working group is developing a P2P network of academic applications. This project is called LionShare, based on the second generation of network technology, more detail is Gnutella model. The main purpose of this network is to allow many users to share different academic institutions of academic material. LionShare network using hybrid type P2P networks, mixed networks and Gnutella decentralized P2P conventional C / S network. Users of this program can upload files to a server, regardless of whether the user is online, we can continue to share. The network also allows the use of a shared community is much smaller than in normal.
The main differenceThe network with other P2P networks currently in use is LionShare network does not allow anonymous users. The aim is to prevent copyrighted material shared on the network, which also avoids a legal dispute. Another difference is that there is a selective sharing individual files for different groups. Individual users can select which users can receive this document or this set of files.
academic community needs this technology, because there are more and more multimedia file applications in the classroom. More and more professors use multimedia files, such as audio files, video files and slideshows. These files are passed to the students is a difficult task, and that if LionShare such networks is much easier.
disputed
legal
In the United States law, jurisprudence "Betamax decision" insistence copy "technology" is not illegal nature, if they have a substantial noninfringing uses. Decided before the widespread use of the Internet is used in most data networks, including P2P networks, as has been recognized by the spread of files is also possible. These include the use of illegal violations of open-source software, public domain works and documents are not within the scope of copyright. Other judiciary also be a similar way of looking at this situation.
In fact, most on P2P file sharing networks is copyright popular music and movies, including a variety of formats (MP3, MPEG, RM, etc.). In most judicial scope, the share of these replicas are illegal. This makes many observers, including most media companies and some P2P advocates criticized the network has caused a huge threat to the existing distribution model. Some studies have attempted to measure how much significance the actual pecuniary loss is unknown. Despite these networks on paper it caused a lot of loss, and in fact since the network is completed, the actual income and not much change. Regardless of whether such a threat exists, Recording Industry Association of America and the Motion Picture Association of America are spending a lot of money to try to lobby lawmakers to create a new law. Some copyright owners also want to help the company to pay the legal challenge to engage in illegal users to share their material.
Despite the Betamax decision, P2P networks have become the target of attacks on behalf of artists and copyright licensing organizations. This includes the American record industry organizations and associations such as the American Film Institute. Napster service due to the complaint of the Recording Industry Association of America were forced to close. In this case, Napster deliberately trading these did not get audio and video files that issued the license from the copyright owner.
With the behavior of media companies to expand the fight against copyright infringement, these networks are also constantly made adjustments quickly, let it technically or in terms of the law are difficult to remove. This leads users to truly break the law becomes the target, because although the underlying technology is legal, but its abuse by way of personal copyright infringement to spread is clearly illegal.
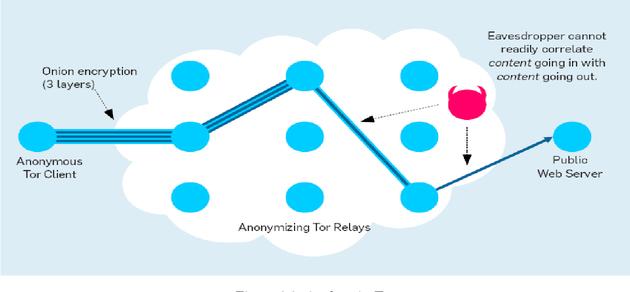
Anonymous P2P networks allow release material, regardless of the legal illegal, have little or no legal liability in the various judicial scope. A lot of people said this would lead to more illegal material is more easily transmitted, even (some people pointed out) the promotion of terrorism, requires it to regulate in these areas. While others objected that the illegal use of the potential of this technology as a not prevent the use of legitimate purposes, the presumption of innocence must be applied, like other non-anonymous P2P technology services, such as e-mail, also has similar capabilities.
safety
Many P2P network has been cherished for various purposes who sustained attack. Examples include:
-
poisoning attacks (providing content and describe different file)
-
Denial of Service (the network run very slowly even completely collapse)
-
betrayal attack (vampire) (user or software using the network did not contribute their own resources)
-
insert the virus in the data (such as downloading or transfer files may be infected with a virus or Trojan)
-
P2P software itself Trojan (such as the software may contain spyware)
-
filtering (network operators may try to ban the transfer of data from the P2P network)
-
identity attacks (such as, network user and performs tracking
spam (e.g., unsolicited sending network information on the type of constant harassment or attack them)
- with the legitimacy - not necessarily denial of service attack)
If well-designed P2P networks use encryption technology, most of the attacks can be avoided or controlled, secure P2P network have in fact closely with Byzantine fault tolerance connect. However, when many nodes trying to destroy it, almost any network will also fail, but many of the agreements due to failure appeared very few users.
On April 23, CA-owned company issued a security alert, pointed out that Foxy, BitComet, eDonkey, μTorrent, Ares, Azureus, BearShare, Lphant, Shareaza, Hamachi, exeemlite, Fpsetup, Morpheus, iMesh 3.14 P2P software and other security threats, potential sources of these threats include P2P software might overwrite files for file rename, delete files, third party malicious programs.
computing technology foresight
technical point of view, strictly speaking, peer networks such as the two sides strictly and equally provision and use of data, there is no difference between server and client. But such pure P2P networks and very few applications, most of the P2P network and application referred to in fact contain some non-dependent or equivalent means such as DNS. At the same time applications actually use more than one protocol, the nodes can be simultaneously or time to become a client, server, and peer nodes; such as Usenet (1979) and FidoNet (1984 years) this has been used for many years to fully distributed peer network.
Many systems use more P2P peer (called a super peer (Super Node)) as a server, that client nodes connected to the star in a super peer.
In the late 1990s, long before the popular instant messaging, in order to promote the development of network applications peer, Sun (SUN) companies to increase in Java technology tired some of the like , so that developers can develop applications and real-time chat applet is not controlled by the central server. This work is now to continue the JXTA project.
P2P systems and applications have attracted a lot of attention to computer science, there (covering the emerging network of a self-organized), including Chord plan, ARPANET, the PAST storage utility, P-Grid in this area , and CoopNet content distribution system including a series of excellent research programs.
Latest: A leaf Guanyin
Next: Inorganic glass








